Executive Summary
Imagine a scenario where malicious actors don’t need to trick you into giving up your password. They have no need to perform sophisticated social engineering attacks or exploit vulnerabilities in your operating system. Instead, they can simply force your computer to authenticate to an attacker-controlled system, effectively commanding your machine to hand over valuable credentials. This attack method is called authentication coercion.
While authentication coercion attacks such as PrintNightmare became well-known in the past few years, we have recently observed a growing trend of a new type of authentication coercion attack. These attacks focus on exploiting rarely used protocols, and they may pass through defenses written specifically for the existing known exploits.
We provide a practical guide to understanding and better defending against this prevalent, highly effective threat. Authentication coercion attacks misuse a fundamental Windows feature that enables computers to execute procedures on remote machines. Attackers manipulate this feature to force machines, including the most critical Tier 0 assets like Domain Controllers, to authenticate to attacker-controlled systems. This attack leverages the design of legitimate authentication protocols in Microsoft Windows environments and requires no special permissions.
We analyze real-world examples of threat actors misusing these inherent Windows authentication mechanisms. Our comprehensive breakdown covers the flow of authentication coercion, and includes a case study of a real attack in which threat actors exploited an obscure, rarely monitored remote procedure call (RPC) interface.
Security researchers, including Unit 42, have documented the use of coercion tools such as PetitPotam (CVE-2021-36942) in actual attacks. Microsoft has issued security advisories acknowledging the exploitation potential of this CVE.
We offer actionable monitoring, detection and prevention strategies that organizations should implement to help identify behavioral anomalies and suspicious RPC packets, for more effective detection and response.
Palo Alto Networks customers are better protected from the threats discussed above through the following products:
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | Privilege Escalation, Windows |
Overview of Authentication Coercion
At its heart, authentication coercion involves manipulating a target’s machine into initiating an authentication attempt to an attacker-controlled server. When a Windows machine attempts to connect to a resource like a shared directory or a printer, it needs to automatically authenticate to the remote resource. Attackers exploit this auto-authentication behavior. By setting up a malicious listener, they can trick a targeted machine into believing the attacker’s system is a legitimate resource it needs to connect to. When the targeted machine attempts to connect, it sends its hashed credentials to the attacker. Figure 1 shows the simplified scenario.
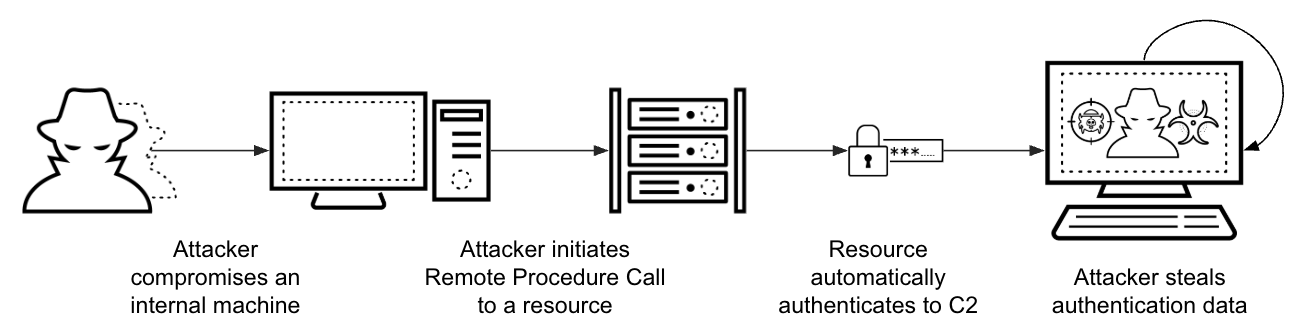
Successful authentication coercion attacks can result in complete domain compromise. This allows attackers to steal sensitive data, deploy malware across networks, and establish persistent access that can remain undetected for extended periods.
What makes this attack method particularly concerning is the widespread availability of proof of concept (PoC) code repositories on platforms like GitHub, which significantly lower the barrier to entry for potential attackers. The availability of ready-to-use exploit code and its integration into penetration testing frameworks like Metasploit, and its use with tools like Mimikatz, have resulted in practical attack methods. Now, even adversaries with minimal technical expertise can deploy these attacks.
Several authentication coercion techniques have been documented in real-world attack scenarios. In May 2022, the Cybersecurity and Infrastructure Security Agency (CISA) reported that a Russian state-sponsored group was exploiting PrintNightmare, CVE-2021-34527. This exploit enabled the threat actor to access cloud and email accounts and exfiltrate documents. CISA lists this CVE in its Known Exploited Vulnerabilities catalog. What this catalog doesn’t show is that attackers are now leaning towards exploiting rare, unseen RPC functions to avoid detection by traditional defense mechanisms.
Under the Hood: Authentication Coercion Techniques
RPC: The Backbone of Windows and Active Directory
To understand authentication coercion, we need to examine the basics of RPC messages. RPC is a fundamental inter-process communication (IPC) mechanism deeply embedded within every Windows operating system. It enables programs to execute procedures and services, whether those services reside locally on the same machine or remotely across a network. RPC is often accessible to standard or low-privileged domain user accounts. RPC functions are executed by calling specific methods on available interfaces, which involves a client sending a request to a server. Each of these methods has a unique operation number (opnum) within its interface that defines the specific action that the operation performs.
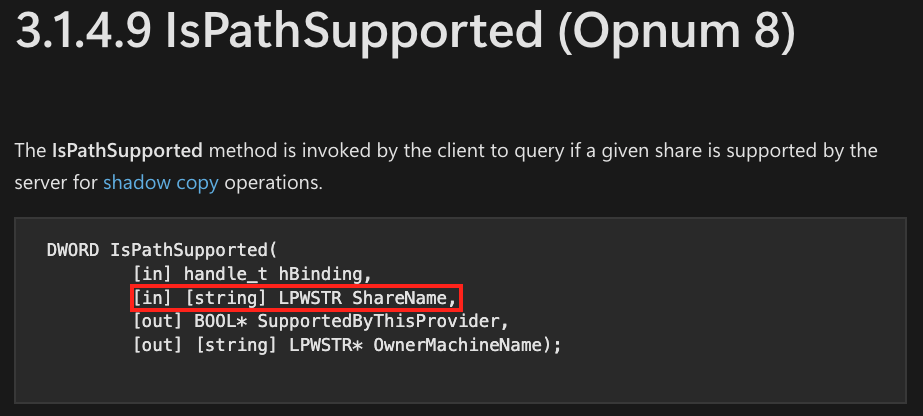
Many Windows protocols utilize RPC functionality as their underlying communication framework. Some functions can operate locally within a system, while others are designed for remote execution. Remote function calls can accept a Universal Naming Convention (UNC) path as a parameter to facilitate communication with a remote machine – for example, \\share\path\to\file. Figure 2 shows an example of an RPC function that takes a UNC format parameter (ShareName).
Misusing Rare RPC Interfaces
In recent years, several RPC functions have become closely associated with coercion techniques. For instance, the PrintNightmare exploit that uses the RpcRemoteFindFirstPrinterChangeNotificationEx function is well known, and already commonly covered by security tools. However, there are other publicly available exploitation and proof of concept tools that simplify the execution of these complex attacks. This has caused security teams to often focus on monitoring the interfaces and functions targeted by those tools. But as defenders harden these known vectors, attackers increasingly pivot to lesser-known opnums that are unlikely to be monitored. For example, a Windows Coerced Authentication Methods repository lists 16 working functions across five protocols that threat actors can use to launch a coercion attack. The author of this repository notes that over 240 functions are yet to be tested, and could possibly be exploited in the same way. Understanding the scope of the attack surfaces that are potentially vulnerable to these common attack tools is crucial for implementing foundational defenses.
Table 1 maps well-known authentication coercion attack tools and the RPC protocols that are vulnerable to them.
| Common Exploit/Attack Tool | Protocol |
| PrinterBug (PrintNightmare) | MS-RPRN
(Print System Remote Protocol) |
| PetitPotam | MS-EFSR
(Encrypting File System Remote Protocol) |
| DFSCoerce | MS-DFSNM
(Distributed File System Namespace Management Protocol) |
| ShadowCoerce | MS-FSRVP
(File Server Remote VSS Protocol) |
| PrintNightmare | MS-PAR
(Print System Asynchronous Remote Protocol) |
| CheeseOunce | MS-EVEN
(EventLog Remoting Protocol) |
Table 1. Publicly known coercion exploits and attack tools, and their corresponding RPC protocol.
Real World Case Study: Using Rare RPC Functions
This section explores a real-world attack in which threat actors used rare RPC functions to conduct authentication coercion attacks.
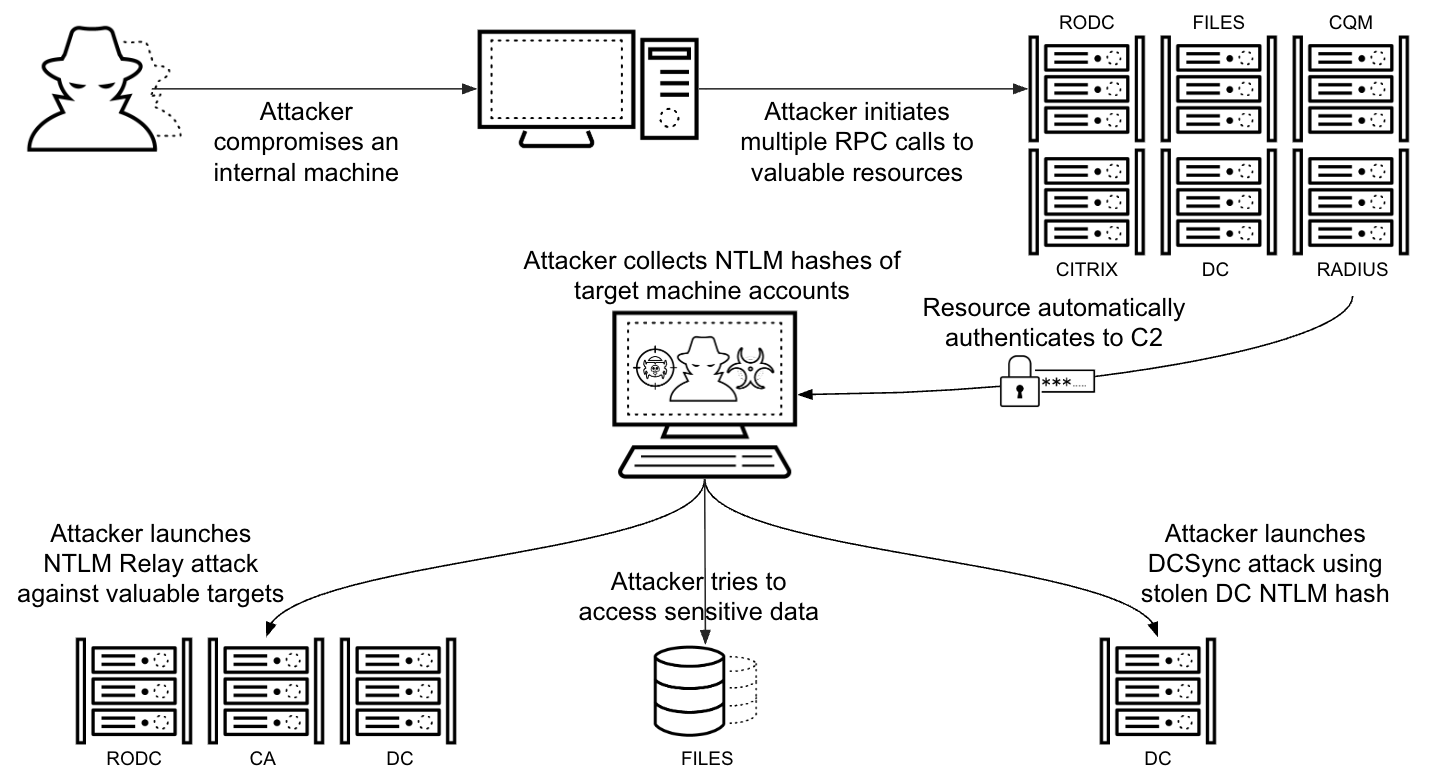
In March 2025, we detected possible coercion activity on several servers within the network of a healthcare industry organization. The alert indicated that a machine on the network was attempting to coerce the local server into contacting an external IP address via RPC. The attacker exploited the remote event logging (MS-EVEN) interface, using a publicly available attack tool. MS-EVEN exposes the RPC methods for reading events in both live and backup event logs on remote computers. The combination of this interface and function is rare in the organization, because no other machine had used that specific protocol in the preceding 30 days. Figure 3 shows the alert this attack triggered.
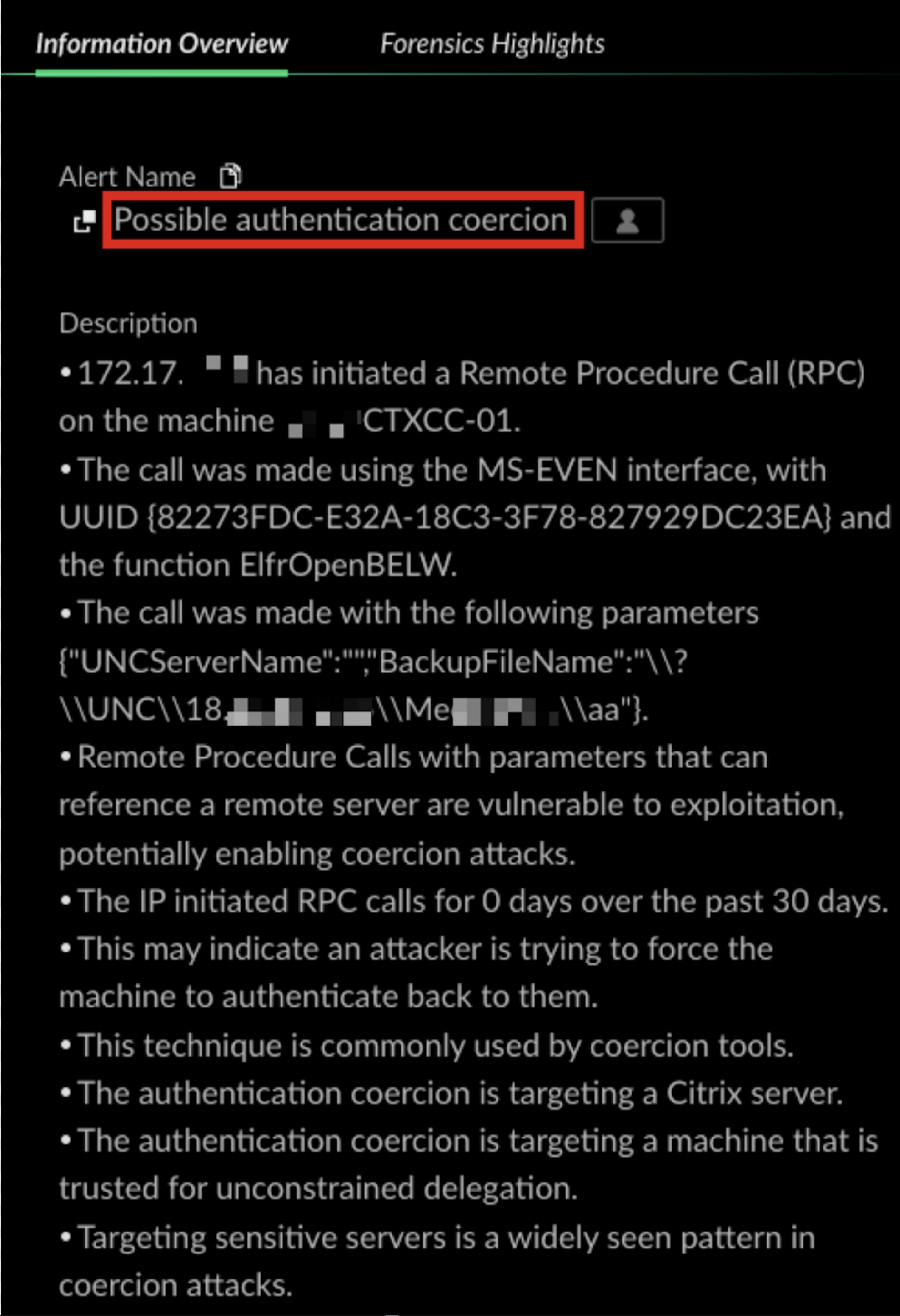
The Cortex XDR “Possible authentication coercion” alert shown in Figure 3 revealed the following artifacts:
- The internal IP address that initiated the remote RPC: 172.17.XX.XX
- Two user accounts that logged in to the internal compromised IP address that day
- The IP address that was parsed from the RPC’s parameters
The threat actor used the ElfrOpenBELW function to execute the coercion attack. Figure 4 shows a detailed explanation of the opnum.
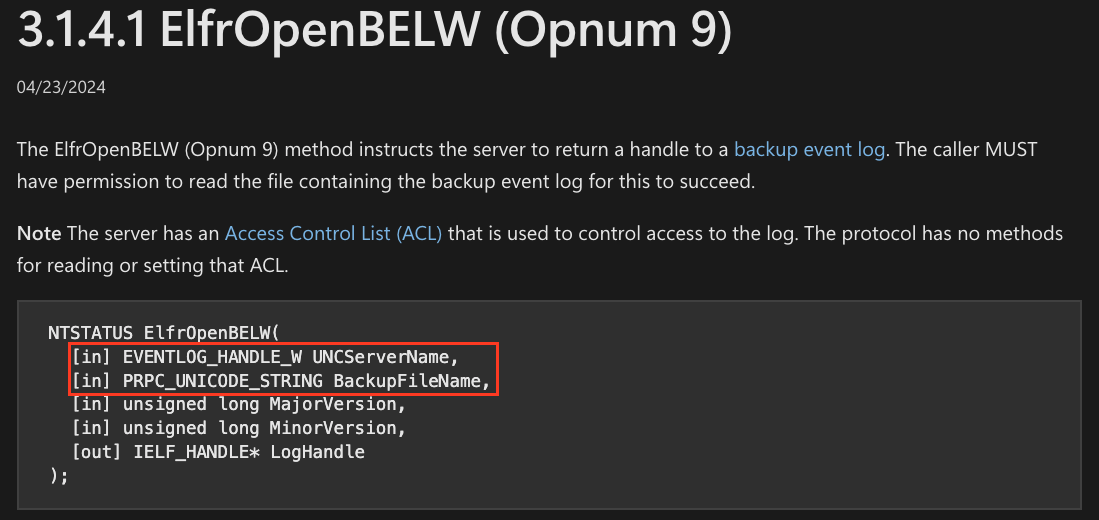
Figure 5 shows the legitimate usage of MS-EVEN when connecting to a remote server in the “Event Viewer” console.
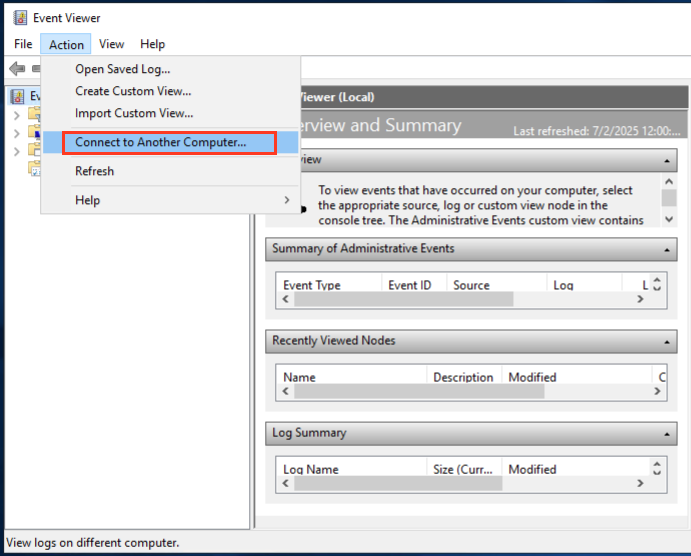
In this example, the IP address used in the ElfrOpenBELW function was external to the organization. The first successful authentication that day occurred at 5 a.m. from an external Kali Linux machine. The absence of malicious activity on the user account indicates that the threat actor had compromised the user’s account prior to the attack. Following these initial connections, the internal IP address then attempted to authenticate using NTLM to a wide range of critical servers within the organization, including:
- Domain Controllers
- Read-Only Domain Controllers (RODC)
- RADIUS servers
- Citrix servers
All of these authentication attempts occurred in a short time window, and all failed. The actor then made those critical servers initiate authentication to an attacker-controlled machine, stole the NTLM hashes of the servers, moved laterally and escalated privileges. Figure 6 shows the RPC actions performed by the compromised host on a wide variety of servers in the organization.
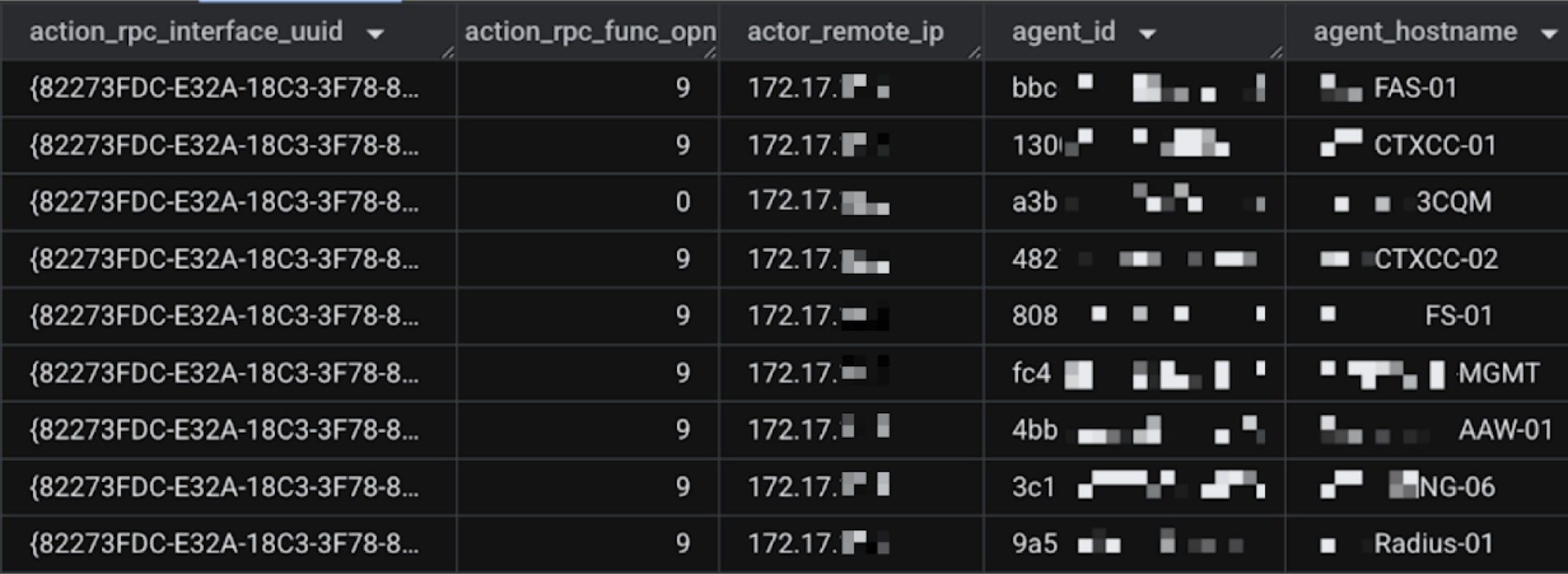
This behavior stood out due to several reasons:
- The rarity of usage for this RPC interface and opnum
- The number of RPC messages and protocols initiated by the machine within a short timeframe
- The RPC message parameters
- The rarity of network traffic to the IP address from the UNC parameter
This behavior is similar to how automatic attack tools work, and it triggered an alert to the organization indicating that an attack might be occurring.
Because RPC authentication coercion does not require special permissions and can be done from any machine with network access to the remote server, the attacker used this method as the primary way to obtain credentials. We observed that the attacker sent malicious RPCS to more than 10 remote resources. All of the calls were from the same machine, and all failed to authenticate via NTLM.
Figure 7 shows the log of the agent rule that prevented the execution of the attack.
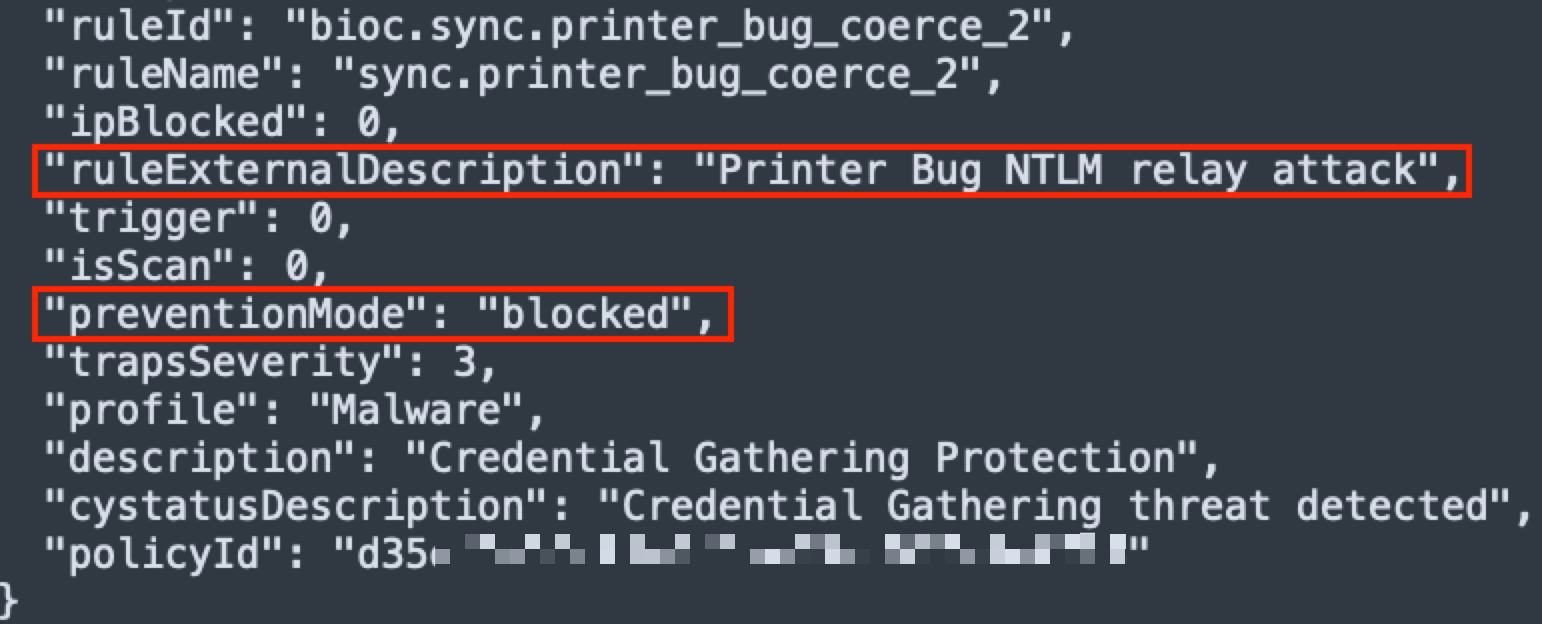
The attacker successfully evaded some of the agent's preventions and forced a Citrix server and an RODC to authenticate to its command and control (C2) servers.
One hour later, the attacker performed an NTLM relay from the same internal IP address. The attacker used the machine account hash of the compromised Citrix and RODC servers to target certificate authority (CA) servers. Figure 8 shows the relayed authentication from a DC machine account to a CA server from the attacker-compromised IP address. The attacker also tried to initiate a DCSync attack with the stolen DC hashes.
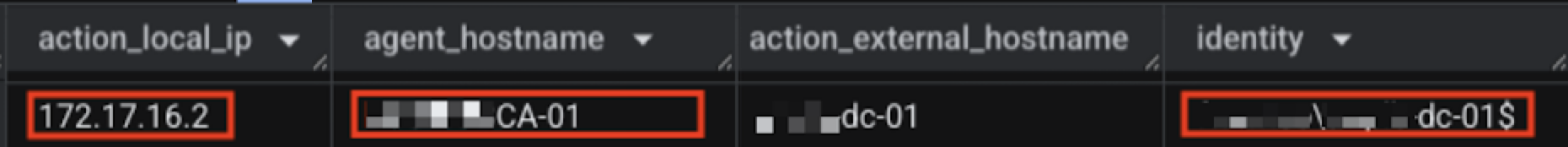
Figure 9 shows a summary of the attacker’s actions.
This attack’s exploitation of rarely used protocols is a growing trend. Our internal telemetry reveals an increase in authentication coercion attacks against organizations, with threat actors misusing unique protocols and functions. One of the main reasons for this increase is that as defense tools evolve and improve, attackers find more diverse and as-yet undetected ways to execute their attacks. This cycle means that defenders must create more advanced approaches to detection.
Don’t Get Coerced: Detection and Prevention Mechanisms
Monitoring RPC traffic is a crucial first step for detecting suspicious activity. However, such monitoring presents significant challenges, due to the sheer volume and complexity of RPC communications. Defenders can better filter out benign RPC traffic and identify malicious coercion activity by following the advice below.
Generic RPC Monitoring and Detection
Effective generic RPC detection involves identifying suspicious attributes and their relevance to various resources. To improve performance and effectiveness in analyzing RPC events, it is essential to filter non-relevant messages. More importantly, security teams should search for anomalies in RPC traffic. This could include:
- UNC path parameters: Various coercion techniques exploit UNC paths. As local RPC traffic is less likely to be suspicious, consider filtering out calls that are performed locally. Investigate RPC parameters that might look malicious or that point to a suspicious IP address.
- Source and destination: Track RPCs that have unusual origin or destination combinations, or calls that target critical assets.
- Interface GUID and opnum: Each RPC protocol has multiple opnums that attackers can use to coerce authentication to a remote server. To help identify such attempts, monitor calls to both rare and known vulnerable interfaces (e.g., MS-RPRN, MS-EFSR, MS-DFSNM, MS-FSRVP) and their specific opnums.
RPC Prevention and Hardening
Improving the detection strategy for RPC communication is a key factor in eliminating coercion attacks. Critical protocols that must remain enabled require more tailored detections, while other RPC-based protocols can be handled in a more generic manner. The following actions can help to prevent coercion attacks from happening at an early stage:
- Windows RPC filters: Windows offers built-in mechanisms to filter RPC traffic, which defenders can leverage to block known coercion techniques. Administrators can use the netsh rpc filter utility to better control and block RPC traffic based on various conditions.
- SMB signing enforcement: Reinforce security by enforcing SMB signing across the domain. While this is not a direct RPC mitigation, it makes it more difficult for threat actors to relay coerced authentications.
- Extended Protection for Authentication (EPA): EPA is a Windows security feature designed to better protect authentication credentials during network connections. Microsoft documentation provides further details about implementing this feature.
- Disable unused RPC services: Minimize the attack surface of assets by disabling unused RPC-based services on them. Permit only needed services that align with the asset’s purpose.
Table 2 provides extensive information for detecting well-known coercion attacks.
| Protocol | SMB Pipe | Interface GUID | Key Functions (Opnums) | Common Exploit/ Attack Tool |
Primary Mitigation |
| MS-RPRN
(Print System Remote Protocol) |
\pipe\spoolss | 12345678-1234-abcd-ef00-0123456789ab | RpcRemoteFindFirstPrinterChangeNotification (opnum 62)
RpcRemoteFindFirstPrinterChangeNotificationEx (opnum 65) |
PrinterBug (PrintNightmare) | Disable Print Spooler service on Domain Controllers; enforce SMB signing |
| MS-EFSR
(Encrypting File System Remote Protocol) |
\PIPE\efsrpc
\PIPE\lsarpc, \PIPE\samr, \PIPE\lsass, \PIPE\netlogon |
c681d488-d850-11d0-8c52-00c04fd90f7e
df1941c5-fe89-4e79-bf10-463657acf44d |
EfsRpcOpenFileRaw (opnum 0)
EfsRpcEncryptFileSrv (opnum 4) EfsRpcDecryptFileSrv (opnum 5) EfsRpcQueryUsersOnFile (opnum 6) EfsRpcQueryRecoveryAgents (opnum 7) EfsRpcFileKeyInfo (opnum 12) EfsRpcDuplicateEncryptionInfoFile (opnum 13) EfsRpcAddUsersToFileEx (opnum 15) EfsRpcFileKeyInfoEx (opnum 16) |
PetitPotam | Enable Extended Protection for Authentication (EPA) and disable HTTP on AD CS servers; disable NTLM on AD CS servers; disable EFSRPC service if not needed |
| MS-DFSNM
(Distributed File System Namespace Management Protocol) |
\PIPE\netdfs | 4fc742e0-4a10-11cf-8273-00aa004ae673 | NetrDfsAddStdRoot (opnum 12)
NetrDfsRemoveStdRoot (opnum 13) |
DFSCoerce | Enforce SMB/LDAP signing; disable NTLMv1 authentication; limit Kerberos unconstrained delegation |
| MS-FSRVP
(File Server Remote VSS Protocol) |
\PIPE\FssagentRpc | a8e0653c-2744-4389-a61d-7373df8b2292 | IsPathSupported (opnum 8)
IsPathShadowCopied (opnum 9) |
ShadowCoerce | Disable “File Server VSS Agent Service” if not needed |
| MS-PAR
(Print System Asynchronous Remote Protocol) |
\PIPE\spoolss | 76f03f96-cdfd-44fc-a22c-64950a001209 | RpcAsyncOpenPrinter (opnum 0) | PrintNightmare | Disable Print Spooler service on Domain Controllers; enforce SMB signing |
| MS-EVEN
(EventLog Remoting Protocol) |
\PIPE\even | 82273fdc-e32a-18c3-3f78-827929dc23ea | ElfrOpenBELW (opnum 9) | CheeseOunce | Disable remote eventlog on Domain Controllers; general NTLM relay protections apply |
Table 2. RPC protocols, interfaces and opnums to detect publicly known coercion attack techniques.
Conclusion
Authentication coercion, particularly through the misuse of rarely monitored RPC interfaces, represents a significant and evolving challenge in securing Windows and Active Directory environments. While traditional defenses against coercion provide sufficient protection against known techniques, these protections are no longer enough. Attackers are now using unmonitored, rare RPC functions – so defenders must seek out these hard to detect coercion methods.
The reliance on RPC across Windows infrastructure creates a broad attack surface. To stay ahead of potential threats, organizations must move beyond monitoring specific publicly available attack tools and PoCs to embrace generic, context-aware RPC monitoring. This means actively searching for anomalies – not just in well-known coercion vectors, but also for less-frequently used RPC interfaces and functions. Practices like establishing behavioral baselines and collecting and leveraging advanced analytics are no longer optional, but essential.
By proactively identifying and responding to these subtle shifts in attacker methodology, organizations can significantly improve their security posture and build more resilient defenses against adversaries.
Palo Alto Networks customers are better protected from the threats discussed above through the following products:
- Cortex XDR and XSIAM
- User and Entity Behavioral Analytics (UEBA) is designed to detect authentication and credential-based threats by analyzing user activity from multiple data sources including endpoints, network firewalls, Active Directory, identity and access management solutions, and cloud workloads. Cortex builds behavioral profiles of user activity over time with machine learning. By comparing new activity to past activity, peer activity and the expected behavior of the entity, Cortex better detects anomalous activity indicative of credential-based attacks.
- Unit 42 Managed Detection and Response Service delivers continuous 24/7 threat detection, investigation and response/remediation to customers of all sizes globally.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Additional Resources
- Searching for RPC Functions to Coerce Authentications in Microsoft Protocols — Remi Gascou, Black Hat 2022
- How RPC Works — Microsoft documentation
- Known Exploited Vulnerabilities Catalog — U.S. Cybersecurity and Infrastructure Security Agency
- Russian State-Sponsored Cyber Actors Gain Network Access by Exploiting Default Multifactor Authentication Protocols and “PrintNightmare” Vulnerability — U.S. Cybersecurity and Infrastructure Security Agency
- Manic Menagerie 2.0: The Evolution of a Highly Motivated Threat Actor — Unit 42
- Threat Brief: Windows Print Spooler RCE Vulnerability (CVE-2021-34527 AKA PrintNightmare) — Unit 42










 Get updates from Unit 42
Get updates from Unit 42